1
Create an application with your OIDC provider
For example, in Okta, once you create an account, you can click on Applications on the sidebar menu:

2
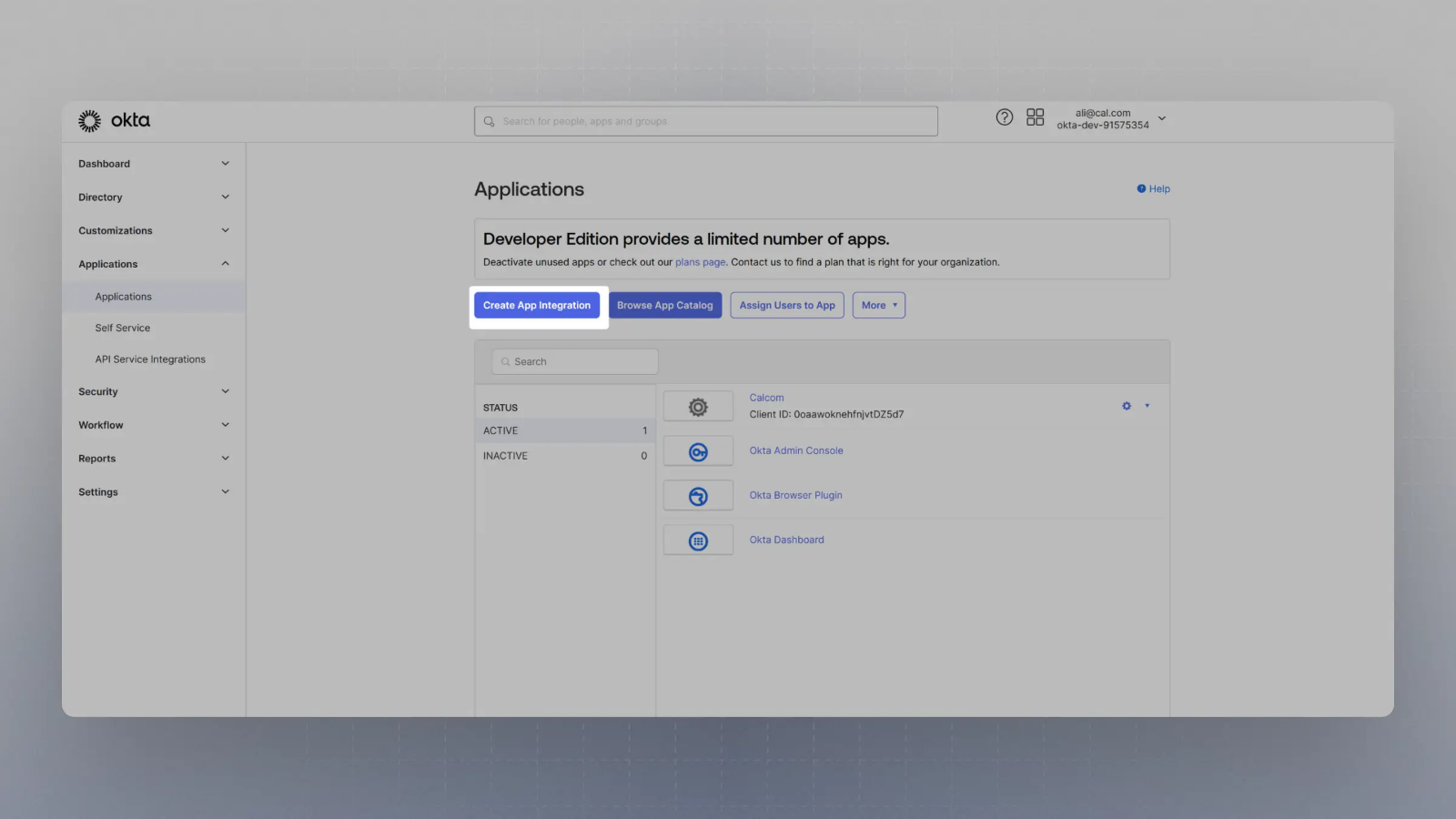
Click on Create App Integration
3
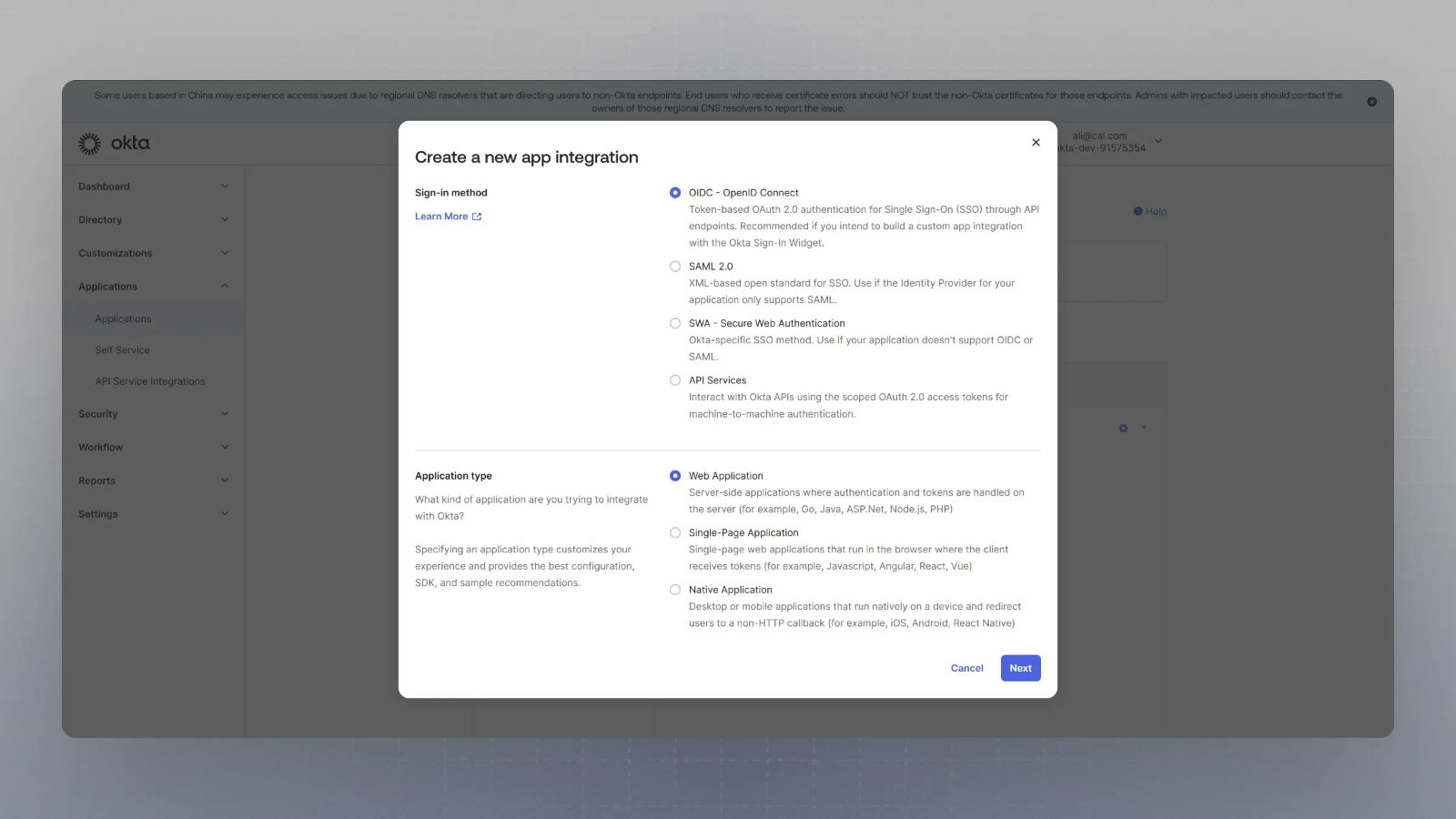
Select OIDC in the modal form, along with Web App, and click Next
4
Enter the Sign in redirect URL and sign out URL
Enter the Sign in redirect URL (or auth URL) as:And the sign out URL as: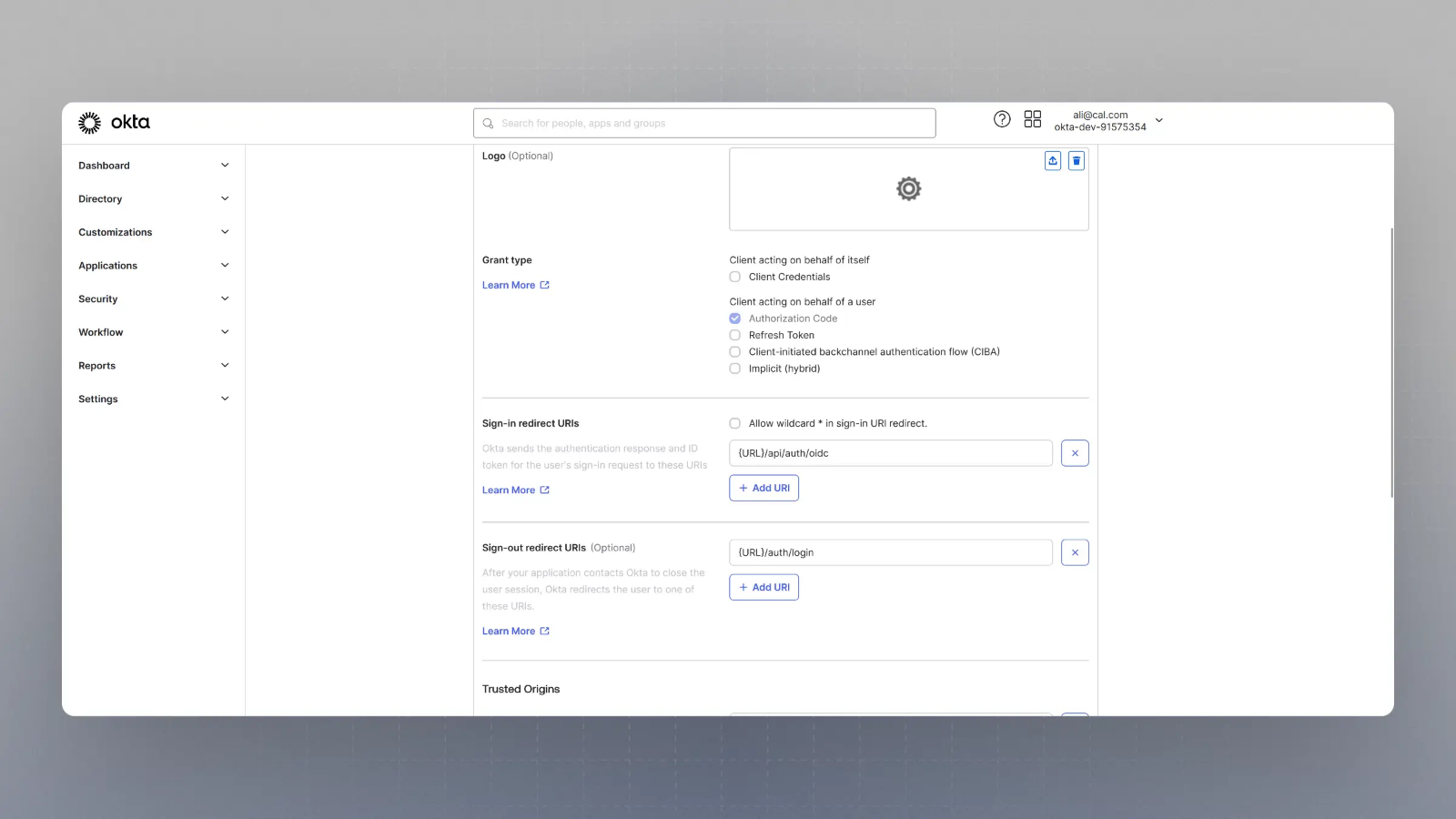

5
Gather Client Secret, Client ID, and Well Known URL
Now you should have the Client Secret and Client ID with you. You would also need the Well Known URL which for Okta is generally of the type:So, if your Okta domain is
dev-123456.okta.com, your well known URL would be:6
Log in
Log in with the Organization Admin user.
7
Go to Organization SSO Settings
Visit 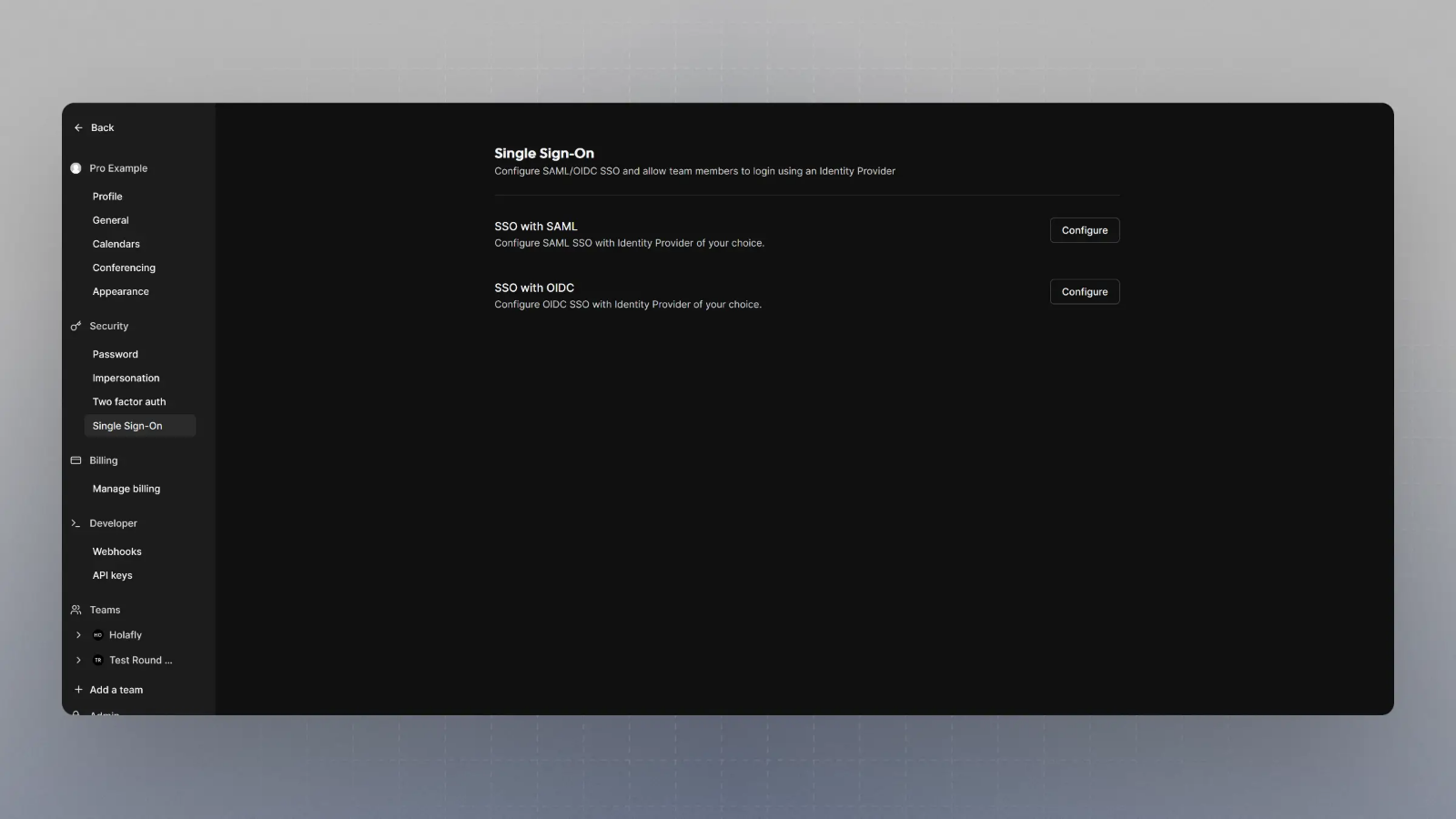
https://app.cal.com/settings/organizations/sso and you should see something like this:
8
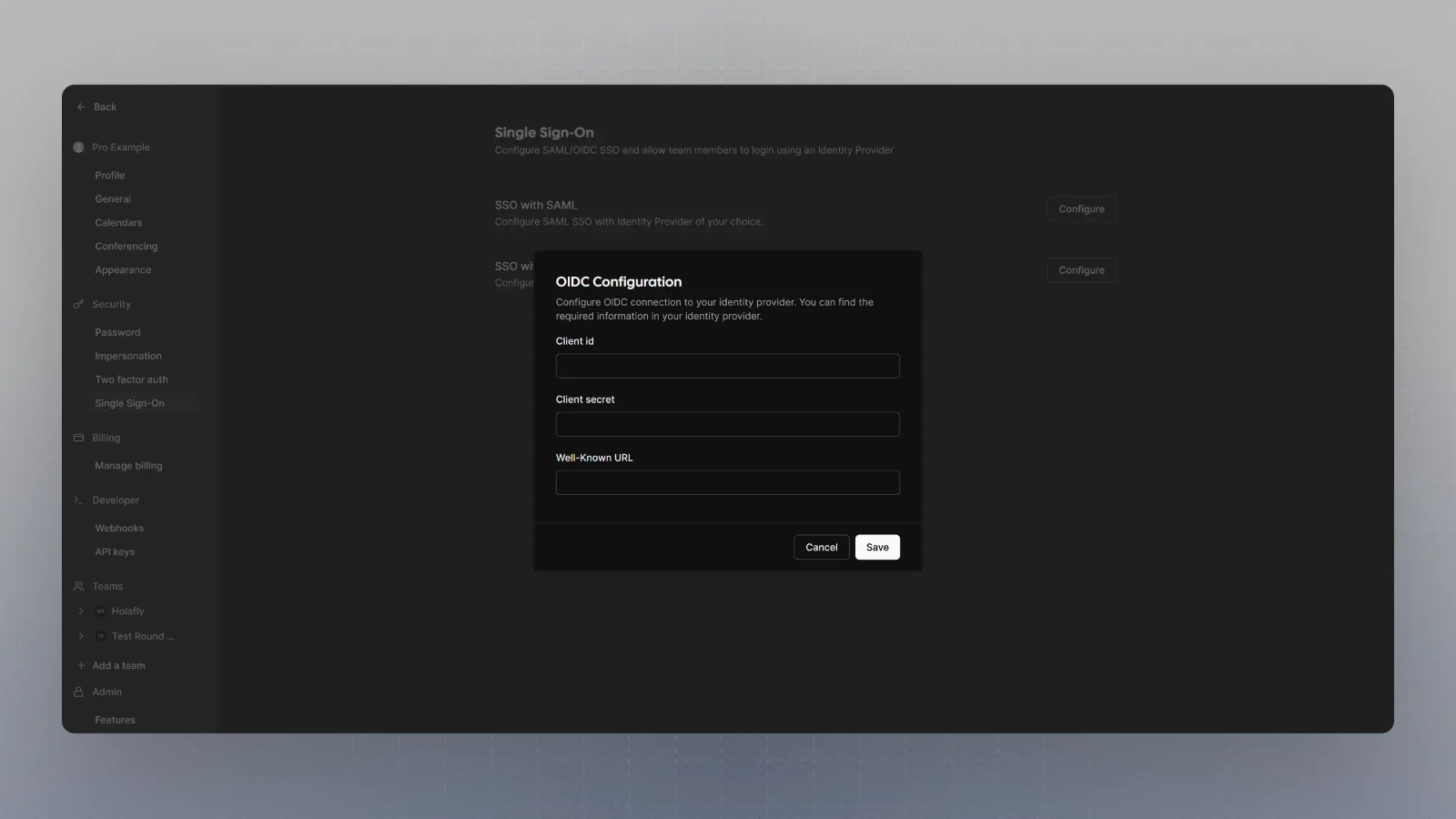
Configure SSO with OIDC
Click on Configure SSO with OIDC, and then enter the Client Secret, Client ID, and Well Known URL from Step 5, and click save.