Secure scheduling infrastructure for enterprise teams
Cal.com gives your organization modern scheduling with built-in SOC 2, HIPAA, and ISO 27001, no extra steps.
01
Domain-wide delegation
Simplify setup and ensure compliance across your organization. Cal.com gives administrators centralized control over calendars, bookings, and access.

02
SAML SSO, SCIM provisioning
SAML SSO, SCIM provisioning, and automated workflows give admins full visibility and control from one dashboard.

03
Privacy compliance tools
Role-based access (RBAC), SAML SSO, and configurable data residency options simplify privacy management across multiple regulatory jurisdictions.

04
Encryption and security monitoring
Cal.com encrypts data in transit and at rest, with continuous monitoring and vulnerability management for ongoing protection.

Information security with every booking
Your scheduling system shouldn’t be the weakest link in your compliance stack. Cal.com’s privacy-by-design architecture gives you the confidence of HIPAA, SOC 2 Type II, ISO 27001, CCPA, and GDPR compliance, without sacrificing usability.





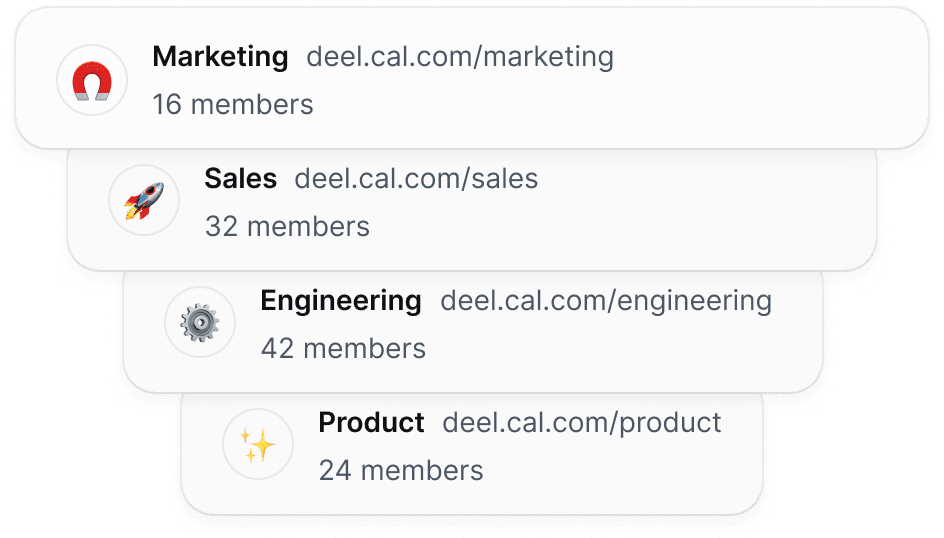
01
Create unlimited sub-teams
Easily organize your teams by creating a parent team and adding unlimited sub-teams, ensuring seamless management and collaboration across your organization.
02
Insights dashboard to analyze bookings
The Insights dashboard provides a clear overview of booking data, helping you spot opportunities and top performers with ease.

03
99.9% SLA
Enjoy guaranteed 99.9% uptime (with an option for 99.99%) with our Service Level Agreement, ensuring your scheduling remains uninterrupted and reliable.

04
Slack Connect for even faster support
We offer Slack Connect support, allowing direct and rapid communication with our team for quicker resolutions and personalized assistance.

01
Round-robin and attribute-based routing
Automatically match bookings to the right person or team by location, specialty, or availability.

02
Shared team pages and routing forms
Manage bookings across distributed teams with centralized control and consistent branding.

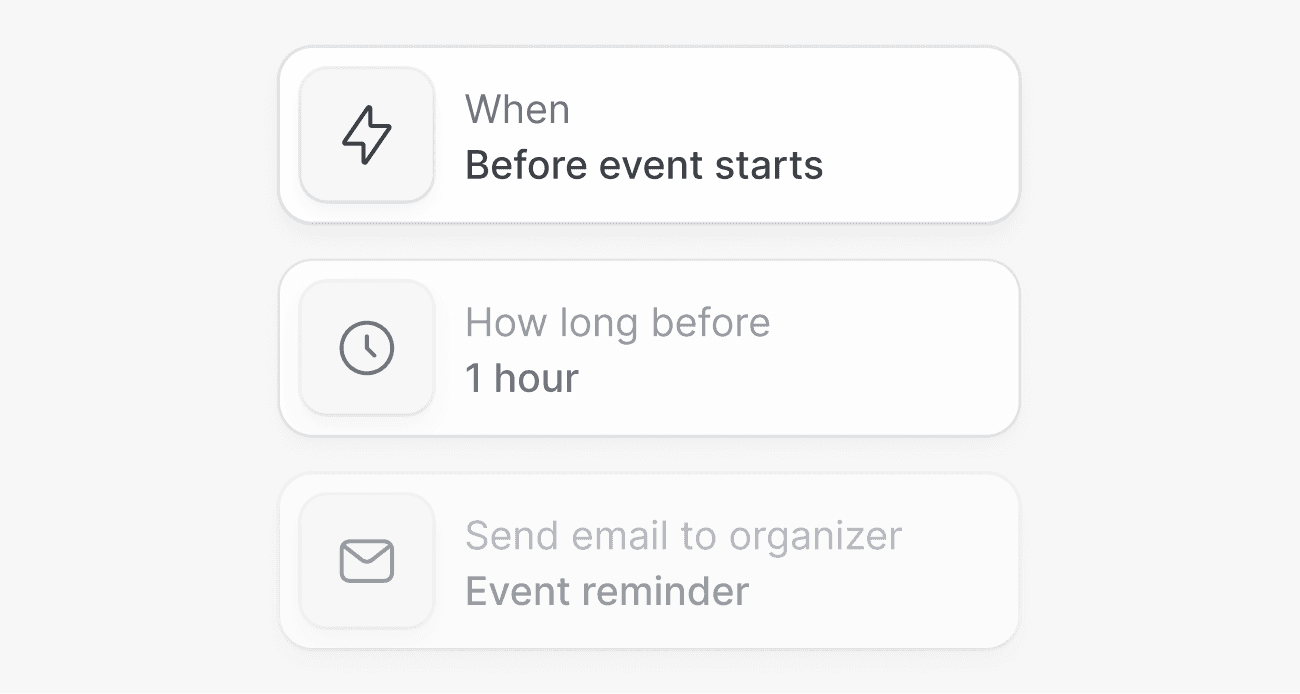
03
Automated reminders
Reduce no-shows and maintain HIPAA compliance with automated voice and SMS scheduling updates.
04
Centralized admin controls
Role-based access and sub-teams bring consistency and compliance to every booking and meeting.

05
Company subdomain
Your company.cal.com subdomain unifies branding, permissions, and data policies across every team.

06
Centralized billing
Streamline reviews, renewals, and access—domain enforcement keeps your workspace secure.

Sales & Marketing
Healthcare & Wellness
Recruiting & HR
Professional Services
Customer success
Higher education
C-suite
Support
Is Cal.com HIPAA compliant?
Yes. Cal.com offers a HIPAA compliant Enterprise plan that includes a signed Business Associate Agreement (BAA) and features designed to protect PHI, such as encrypted data storage, access logging, and customizable intake workflows.
Is Cal.com SOC 2 certified?
Yes. Cal.com maintains SOC 2 Type II certification, verified through annual independent audits covering security, availability, and confidentiality controls.
How does Cal.com differ from other scheduling tools?
Cal.com was built for organizations, not individuals. It combines enterprise-grade security (SSO, SCIM, audit logs) with the simplicity of a modern calendar app, so scaling secure scheduling across teams is seamless.
Can I restrict data access by team or department?
Yes. Cal.com supports role-based access control (RBAC), sub-team structures, and domain enforcement so only authorized users can access or modify sensitive booking data.
Can I use my own branding and get a custom subdomain?
Yes. You can host your scheduling pages on your own company.cal.com subdomain or fully white label Cal.com under your organization’s brand. Customize colors, logos, and booking pages to create a seamless, branded experience.
What support options are available for Enterprise customers?
Enterprise plans include priority support, dedicated onboarding, and optional service-level agreements (SLAs) to ensure smooth implementation and ongoing success.
Simplify scheduling. Strengthen compliance.
Cal.com brings modern scheduling to regulated teams with SOC 2, HIPAA, and total admin control, all in one place.